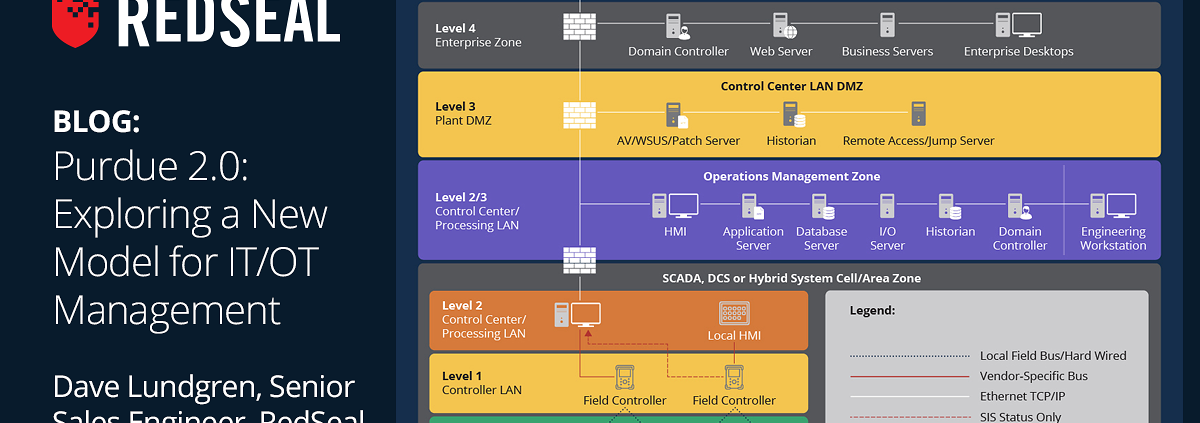
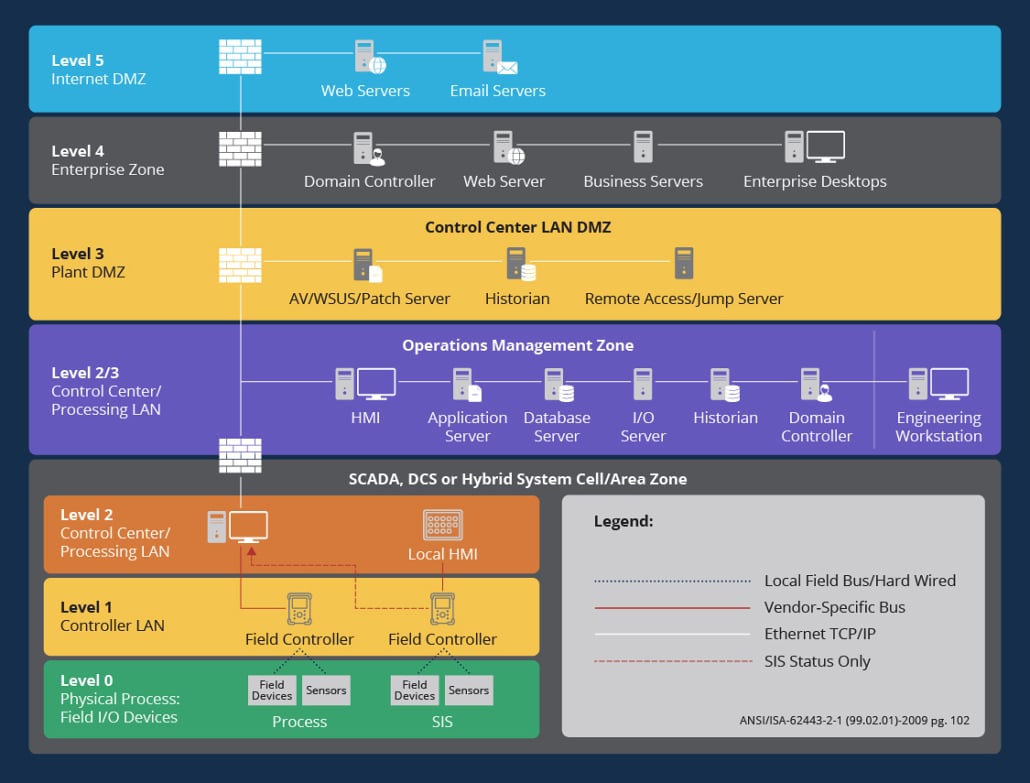
Today’s cloud infrastructure is complex and constantly evolving. In the cloud, security controls are implemented by developers and DevOps teams while on-premises controls are implemented by the firewall/network operations teams. These can create significant knowledge gaps, leading to unknown attack points.
Most security spending these days is focused on the cloud and treated as a silo, but you can’t afford to ignore your on-prem resources and how the two entities work together.
Challenges with Protecting Cloud and On-Premises Resources
With resources moving to the cloud, most of the attention moves to cloud security and protecting the cloud perimeter and resources. Yet on-prem resources also have connections and exposure. However, you need a comprehensive security strategy that protects both cloud and on-premises resources.
Many organizations and vendors struggle with getting this comprehensive picture. For example, in many companies, in-house teams are responsible for managing on-prem resources while other teams or third-party providers monitor the security of cloud resources. At the same time, you have DevOps teams that are constantly evolving the cloud environment.
Different Languages
The products and tools being used in the cloud and on-premises domains are often disconnected and speak different languages as do the teams using them.
The problem is not people, however. It’s often the tools being used, like having a separate doorman on the front door (cloud) and back door (on-prem), and they both speak different languages and often have competing goals. While security teams are focused on mitigating exposure, DevOps teams are looking for a faster way to bring products to market. Competing goals can only aggravate language barriers.
Even highly skilled teams may not understand how other teams work. The technology is different, the configurations are different, and some nuances require expert interpretation and experience. Few team members will be conversant in both on-prem and cloud resources.
Greater Complexity
More than 90 percent of large organizations already employ multi cloud strategies; 80 percent use hybrid clouds.
This creates an even greater complexity for security and management. For example, Amazon Web Services (AWS), Microsoft Azure, and Google Cloud use different names for instances and virtual machines. Azure calls them virtual machines (VMs), while Amazon has Elastic Cloud Compute (EC2) and Google has the Google Cloud Compute Engine.
Even when the same term is used, it can mean different things. For example, a virtual private cloud (VPC) exists in both AWS and Google, but they are different and operate differently.
This only increases the language barrier that hinders a comprehensive approach to security.
Lack of Understanding of Shared Responsibility
Organizations also assume their cloud service provider (CSP) will protect assets in the cloud. While CSPs such as AWS, Azure, Google Cloud, Oracle Cloud, and others provide robust security for their networks, it’s still the customer’s responsibility to protect their data.
Gartner estimates that 99 percent of cloud security failures are the fault of the customer, not the CSP. The sheer volume of configuration settings and pathways to critical resources makes it difficult to manage security in the cloud. When you add in on-premises data centers or servers that are connected, the infrastructure becomes even more complex.
Constant monitoring and continuous compliance should be a shared responsibility between providers and organizations.
Not Monitoring Resource Misconfigurations
Most vendor security solutions are only as effective as how they’re configured. Yet few are monitoring that and telling you where these configurations are causing potential problems.
You need a comprehensive, end-to-end understanding of your cloud and on-prem infrastructure to analyze every configuration and security policy. While you may have cloud security tools for each environment, you need complete cloud network visibility to protect your infrastructure, look for exposure, and find security gaps.
Are You Seeing the Whole Picture?
Nearly every organization has at least some on-premises that are connected. The challenge often comes when it’s time to configure the right access for communication. You need to ensure that nobody on the cloud side can attack on-prem resources or vice versa. That’s why total visibility is essential.
If you’re not seeing the whole picture, it’s easy to miss attack points. Securing your infrastructure requires you to detail what you have, how it’s connected, and what’s at risk.
You need to:
- Know what you have in your total infrastructure
- Understand how everything is connected
- Determine where your exposure is — all attack paths to cloud and on-premises
- Uncover what policies or configurations created the exposure
Only then can you remediate problems and plug security gaps. You must understand how your cloud and on-prem resources are all interconnected to determine and mitigate your total risk.
Managing Cloud and On-Prem Resources
Some organizations turn to Cloud Native Application Protection Platforms (CNAPP) as a way to provide visibility amid the complexities and the constant evolution of hybrid resources. Yet all existing CNAPP solutions don’t understand on-Premises and are insufficient to identify access via all attack path and associated risk. Most tools call into the application programming interfaces of cloud service providers, looking for misconfigurations at the compute and container levels. However, they don’t fully understand end-to-end access.
CNAPP is an important weapon in the battle to secure the cloud, but most vendor solutions simply do not provide the total visibility you need across cloud and on-prem resources. RedSeal solves these problems.
RedSeal on-premises and RedSeal Stratus in the cloud provide a complete view of the entire infrastructure. They identify the gaps in your security by pinpointing attack points and any hidden pathways. This analysis also determines the underlying reason why these attack points exist and what needs to happen to remediate them.
RedSeal solutions also work across borders. They provide the platform to speak to DevOps and firewall/network operations teams in the right way, helping eliminate language barriers. This way, you get benefits across borders for cloud and on-prem, enabling you to identify security issues across the entire infrastructure by driving collaborations between the teams and building trust.
Protect Your Entire Infrastructure
On-premise and cloud resources cannot be protected in a silo. Working in tandem with a shared responsibility model, a hybrid solution with RedSeal provides continuous monitoring and compliance across both on-prem and cloud resources, identifies gaps, and helps you protect your entire infrastructure.