Network Security at Risk: Why Zero Trust is (Still) Non-Negotiable
As organizations expand their digital footprint and shift to more complex, hybrid infrastructures, traditional security models are no longer sufficient to protect critical networks. Relying solely on a “trust but verify” approach is riskier than ever. The solution? Zero Trust. Although Zero Trust has been a recognized security model for years, its importance has never been more urgent.
What is Zero Trust?
Zero Trust challenges the outdated perimeter-based defense strategy by assuming that threats can exist both inside and outside the network. Every user, device, and service requesting access must be authenticated and continuously validated before being granted permissions. This approach minimizes the risk of unauthorized access and lateral movement within the network, making it a cornerstone of modern cybersecurity strategies.
U.S. Treasury Department slammed by breach
In December 2024, the U.S. Treasury Department fell victim to a sophisticated cyberattack attributed to Chinese state-sponsored hackers. The breach occurred after attackers exploited vulnerabilities in BeyondTrust’s remote support software, gaining unauthorized access to unclassified documents and workstations. This attack highlights the critical need for robust security strategies that extend beyond traditional perimeter defenses, especially in complex networks.
Organizations that adhere to Zero Trust framework, minimize attackers’ abilities to move laterally within the network. With Zero Trust’s “never trust, always verify” model, every user, device, and service are continuously authenticated, regardless of location. This approach enables faster detection and response to threats—reducing the impact of breaches.
UnitedHealth Group breach impacts more than originally expected
In February 2024, a breach involving UnitedHealth Group (UHG) and Change Healthcare exposed the data of approximately 190 million individuals, significantly more than the initial 100 million reported. The BlackCat ransomware group infiltrated Change Healthcare’s network through compromised Citrix server credentials that lacked multi-factor authentication. Over several weeks, the attackers moved across the network, stealing personal, health, and financial data. Despite paying a $22 million ransom to prevent data release, the hackers retained the stolen information.
Again, this breach underscores the urgent need for Zero Trust security models in protecting sensitive healthcare data. By implementing continuous access validation and monitoring, the attackers would have encountered tighter controls, limiting their lateral movement. Zero Trust ensures that even if an entry point was compromised, impact would be minimized, providing stronger defense against future cyberattacks.
RedSeal’s role in Zero Trust security
RedSeal’s exposure management platform is key to the Zero Trust model. By providing detailed, real-time insights into your network topology, RedSeal ensures you have the visibility you need to understand exactly how assets, connections, and services are structured. This visibility is crucial to building a strong foundation for Zero Trust, enabling you to discover, investigate, and act to measurably reduce and mitigate risks.
RedSeal’s platform offers:
- Comprehensive visualization: RedSeal brings all connected network assets into a cohesive interactive model to uncover hidden risks.
- Attack path analysis: Only RedSeal reveals all the ways threats can breach and spread throughout the network
- Risk prioritization: With RedSeal, measure true business impact to ensure efficient and effective remediation efforts
- Continuous compliance: Ensure you’re up to date with external requirements, internal policies, and best practices.
Zero Trust target and advanced activities
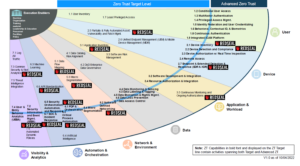
This image from the DoD shows how Zero Trust grows in complexity over time as agencies and enterprises attempt to secure their environments across the seven pillars of Zero Trust.
Strengthening your Zero Trust framework
The successful implementation of Zero Trust relies on granular segmentation, comprehensive asset inventories, and real-time monitoring. RedSeal aids in:
- Macro and micro-segmentation: RedSeal supports both macro-segmentation, which controls access between network segments, and micro-segmentation, which enforces policies within smaller segments, reducing the attack surface.
- Data flow mapping: RedSeal’s ability to map data flows is essential for identifying unprotected paths and ensuring that all sensitive data is properly secured.
With RedSeal’s insights, you gain the visibility, context, and dynamic network modeling necessary to accelerate your Zero Trust journey. Whether you’re managing on-premises resources, cloud environments, or hybrid systems, RedSeal delivers the actionable insights you need to continuously secure and fortify your network.
Interested in learning more? Download our Zero Trust Solution Brief.
Partnering with RedSeal for Zero Trust
For more than 20 years, RedSeal has been a trusted partner for organizations across industries, helping them strengthen their cybersecurity posture. By offering a digital twin of your network, RedSeal enables you to better understand and manage security risks, while aligning with industry best practices for Zero Trust.
Reach out today to learn more about how we can support your Zero Trust journey.



