Cyber News Roundup for September 13, 2024
Recent cybersecurity updates include the National Vulnerability Database (NVD) struggling with a critical backlog, which hampers its effectiveness in vulnerability analysis. SonicWall is dealing with a significant access control vulnerability (CVE-2024-40766) in SonicOS, currently exploited in the wild. Avis has disclosed a breach affecting nearly 300,000 customers. On a positive note, Google Cloud has introduced new air-gapped backup vaults to boost ransomware protection, and MasterCard is set to acquire Recorded Future for $2.65 billion.
Read these stories and more in today’s Cyber News Roundup.
The Fall of the National Vulnerability Database
The National Vulnerability Database (NVD) has experienced a significant slowdown, leaving thousands of vulnerabilities without analysis, which is critical for identifying risks. This has raised concerns in the cybersecurity community, especially as many organizations and government contractors rely on NVD for vulnerability management. The issues stem from a backlog, underfunding, and challenges in handling the increasing volume of CVEs. While alternatives like Open Source Vulnerabilities (OSV) exist, NVD remains essential for many, especially under federal requirements. (Darkreading)
SonicWall vulnerability exploited in the wild
A recently patched access control vulnerability (CVE-2024-40766) affecting SonicWall’s SonicOS is being exploited in the wild, BleepingComputer reports. The vulnerability affects SonicWall Firewall Gen 5 and Gen 6 devices, as well as Gen 7 devices running SonicOS 7.0.1-5035 and older versions. SonicWall urges customers to apply the patch as soon as possible. The company adds, “SonicWall strongly advises that customers using GEN5 and GEN6 firewalls with SSLVPN users who have locally managed accounts immediately update their passwords to enhance security and prevent unauthorized access. Users can change their passwords if the ‘User must change password’ option is enabled on their account. Administrators must manually enable the ‘User must change password’ option for each local account to ensure this critical security measure is enforced.” (Bleepingcomputer)
Car rental company Avis discloses data breach
According to notification letters sent to customers on Wednesday and filed with California’s Office of the Attorney General, the breach, which was discovered last Thursday, saw the unknown threat actor having access to its business applications from August 3 until August 6, resulting in the theft of “some customers’ personal information, including their names and other undisclosed sensitive data.” This is a developing story. (BleepingComputer)
Wisconsin Medicare users had information leaked in MOVEit breach
More fallout from the MOVEIt breach of last year: “the Centers for Medicare & Medicaid Services (CMS), which is a federal agency that manages the Medicare program, as well as the Wisconsin Physicians Service Insurance Corporation (WPS) said on Friday that they have begun notifying people whose personal information leaked after hackers exploited a vulnerability in the MOVEit software.” The discovery follows a second investigation into the breach conducted by WPS in May, after receiving “new information” about the breach. (The Record)
1.7 million impacted in payment processing breach
In an ironic twist, payment gateway provider Slim CD says they’ve swiftly initiated an investigation into a breach affecting around 1.7 million individuals. While the company claims to be moving quickly to address the issue, the breach actually occurred in August 2023 but went undetected until almost a year later in June 2024. Information exposed in the attack includes names, physical addresses, credit card numbers, and payment card expiration dates. Despite the impact, Slim CD has not offered any free identity theft protection services to those affected, instead advising individuals to stay vigilant and order a free credit report. (Bleeping Computer), (The Register)
Avis breach impacts almost 300,000 customers
An update to a story we first brought to you on Monday: Car rental company Avis is now reporting that a breach discovered last week has impacted over 299,000 of its customers, which, according to Bleeping Computer, is less than 1% of the company’s customer base. The threat actor was able to access business applications last month and stole personal information, including names and other undisclosed data. (Bleeping Computer)
New RaaS operation is recruiting criminal affiliates
Palo Alto Networks’ Unit 42 has published a report on Repellent Scorpius, a ransomware-as-a-service operation that surfaced in May 2024. The group distributes the Cicada3301 ransomware and conducts double-extortion attacks by exfiltrating data before deploying the ransomware. The researchers state, “Unit 42 has evidence to suggest that the Repellent Scorpius operators have developed a RaaS affiliate program. It operates a control panel for affiliates and ransom payment pages for victims, and actively recruits initial access brokers (IAB) and network intruders on Russian-language cybercrime forums.” (PalloAlto)
Earth Preta deploys new malware in the Asia-Pacific
Trend Micro is tracking new variants of malware used by the China-aligned threat actor Earth Preta (also known as “Mustang Panda”). The threat actor is using spearphishing emails and removable drives to deploy malware against government entities in the Asia-Pacific region. Trend Micro states, “Earth Preta employed a variant of the worm HIUPAN to propagate PUBLOAD into their targets’ networks via removable drives. PUBLOAD was used as the main control tool for most of the campaign and to perform various tasks, including the execution of tools such as RAR for collection and curl for data exfiltration. PUBLOAD was also used to introduce supplemental tools into the targets’ environment, such as FDMTP to serve as a secondary control tool, which was observed to perform similar tasks as that of PUBLOAD; and PTSOCKET, a tool used as an alternative exfiltration option.” (Trendmicro)
Slim CD notifies 1.7M customers of data breach
Electronic payment firm, ESlim CD, has notified nearly 1.7 million credit card holders that their data may have been stolen after an attacker accessed their systems between August 17, 2023, and June 15, 2024. A third party investigation uncovered the incident on June 15. Slim CD said it reviewed its data privacy and security policies and implemented additional safeguards following the incident. KnowBe4 awareness advocate, James McQuiggan said, “When organizations realize that cybercriminals are inside their network for long periods, there is a gap with continuous security monitoring. Accompanied by a robust Security Incident Management (SIEM) system integrated with threat intelligence, the breach could have been detected sooner.” (SC Media)
Google Cloud introduces air-gapped backup vaults
Google Cloud has introduced air-gapped backup vaults as part of its enhanced Backup and Disaster Recovery (DR) service, now available in preview. These vaults provide robust protection against ransomware and unauthorized data manipulation by creating immutable and indelible backups, preventing modification or deletion until a set retention period elapses. Isolated from the customer’s Google Cloud project, these air-gapped vaults reduce the risk of direct attacks on backups. (Cyber Security News)
Lazarus Group’s VM Connect campaign spoofs CapitalOne
New research from Reversing Labs shows that the Lazarus Group is continuing its campaign of tempting targeting developers with malicious software packages on open-source repositories by posing as employees of the financial services firm Capital One. Again seeking to lure developers into downloading the malware by directing them to a GitHub repository containing a “homework task.” This is similar, but different from a story we reported on last week in which the Lazarus Group was seen doing the same thing through LinkedIn using CovertCatch. In this case Reversing Labs researchers says it is connected to a 2023 VMConnect campaign focused on Python modules. They added, “It is clearly intended to create a sense of urgency for the would-be job seeker, thus making it more likely that they would execute the package without performing any type of security or even source code review first.” (InfoSecurity Magazine)
Mastercard buys Recorded Future
Financial payment company MasterCard announced yesterday that it will acquire the threat intelligence company Recorded Future for $2.65 billion, adding to its current portfolio of security products, which include risk assessments and transaction protection. In its press release, MasterCard noted that “Recorded Future is a well-known intelligence firm that boasts more than 1,900 clients internationally, including 45 governments and over half of Fortune 500 companies.” The firm will remain an independent subsidiary, and the deal is expected to close in the first quarter of 2025. (Cyberscoop)
Have questions? Reach out to RedSeal today to chat with one of our cybersecurity experts.





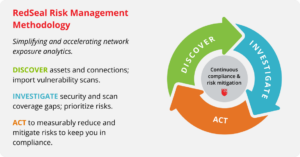 Today, let’s dive into one of our standout features—the Risk tab—and explore how we can use our Risk Management Methodology of Discover, Investigate, and Act to transform your risk management strategy.
Today, let’s dive into one of our standout features—the Risk tab—and explore how we can use our Risk Management Methodology of Discover, Investigate, and Act to transform your risk management strategy.

