Cyber News Roundup for October 4, 2024
Recent headlines highlight significant challenges in cybersecurity across the globe. Cloudflare blocked a massive 3.8 Tbps DDoS attack targeting finance and telecom sectors, while Adobe Commerce faces exploitation of critical vulnerabilities. Agence France-Presse experienced disruptions from cyberattacks, and UMC Health in Texas diverted patients due to a ransomware incident. Major providers like Verizon and PlayStation also faced outages. With state Chief Information Security Officers expressing budget concerns, the urgency for robust cybersecurity measures has never been clearer, emphasizing the need for ongoing vigilance in the face of evolving threats.
Cloudflare blocks largest recorded DDoS attack peaking at 3.8Tbps
This denial-of-service campaign targeted organizations in the financial services, internet, and telecommunications sectors, part of a “month-long barrage of more than 100 hyper-volumetric DDoS attacks flooding the network infrastructure with garbage data.” According to Cloudflare, who successfully blocked the attack, the infected devices used were mostly located in Russia, Vietnam, the U.S., Brazil, and Spain. They consisted of a large number of Asus home routers, Mikrotik systems, DVRs, and web servers. The peak at 3.8 Tbps lasted 65 seconds. (BleepingComputer)
Adobe Commerce and Magento stores compromised by CosmicSting bug
Researchers at Sansec have reported that numerous threat actors have exploited this vulnerability in Adobe Commerce, which comes with a CVSS score of 9.8, and has compromised more than 4,000 e-stores over the past three months. “An attacker could exploit this issue by sending a crafted XML document that references external entities, and exploitation of this issue does not require user interaction.” This vulnerability had been added to the CISA KEV catalog in July of this year. (Security Affairs)
A global news agency suffers a cyberattack
Agence France-Presse (AFP) experienced a cyberattack on September 27, disrupting its content distribution infrastructure, but its core news reporting remains unaffected. The attack targeted AFP’s IT systems, specifically content delivery networks and file transfer services used to deliver news to clients. While the type of attack and the responsible party are still unknown, AFP quickly responded, with the French cybersecurity agency ANSSI assisting in securing the systems. AFP warned clients that their FTP credentials might have been compromised, advising them to update passwords and secure their systems. Despite these technical issues, AFP assured that its newsroom continues to operate without interruptions, delivering news globally in multiple languages. No group has claimed responsibility for the attack so far. (Hackread)
A Texas health system diverts patients following a ransomware attack
UMC Health System in Texas has been diverting patients after a ransomware attack forced them to take their IT systems offline. The incident, disclosed on September 27, led to both emergency and non-emergency patients being diverted to nearby hospitals. UMC launched an investigation and disconnected its systems to contain the breach. By Monday, some services were restored, and only a few patients were still being diverted. UMC’s Emergency Center is now accepting ambulance patients, while other facilities remain open but are not fully operational. The hospital has engaged third-party experts to aid in the recovery process. Downtime procedures have been implemented, and patients are being informed of changes to appointments. UMC continues its efforts to restore services safely and provide updates on the investigation and remediation efforts. (SecurityWeek)
Western Digital patches a critical vulnerability in network attached storage devices
A critical vulnerability, CVE-2024-22170, has been identified in Western Digital’s My Cloud devices, affecting models like My Cloud EX2 Ultra and PR4100. This flaw, with a CVSS score of 9.2, allows attackers to exploit an unchecked buffer in the Dynamic DNS client through a Man-in-the-Middle attack, leading to arbitrary code execution. Western Digital has addressed the issue in a firmware update and urges users to update immediately. The vulnerability poses risks of unauthorized access, data corruption, and system crashes. Western Digital thanks researchers at Claroty for responsibly disclosing the issue. (CyberSecurity News)
Verizon and PlayStation each suffer outages
On Monday morning, thousands of Verizon users across major U.S. cities, including New York, Los Angeles, and Chicago, experienced widespread cellphone service outages. Over 104,000 reports were logged on Downdetector by 11:30 a.m. Eastern, with the number later dropping to 78,000. Many users reported their phones showing “SOS” mode, preventing calls and messages. Verizon confirmed the issue, with engineers working to resolve it, though the cause was unclear. Simultaneously, the PlayStation Network (PSN) faced a global outage, affecting services like gaming, account management, and the PlayStation Store. Sony is working to fix the issue, which began at 8:41 PM ET, with some services still down, potentially due to overloaded servers. Both outages disrupted users’ daily activities and work. (Bleeping Computer) (The New York Times)
A Crypto Criminal Stretches His Limits—And His Legs
And finally, Krebs on Security chronicles an absolutely bonkers mix of cybercrime and corruption straight out of a pulp novel. A California man, Adam Iza (aka “The Godfather”), is accused of not only dodging taxes on millions allegedly earned from cybercrime but also paying off local cops to help intimidate rivals. Iza, co-owner of the cryptocurrency platform Zort, reportedly spent investors’ money on luxury cars, jewelry, and even leg-lengthening surgery. I swear I am not making this up.
According to the FBI, Iza hired Los Angeles Sheriff’s Department officers to help him extort former business partners, some of whom were tied to the notorious hacker group UGNazi. One incident involved trying to steal a laptop full of cryptocurrency, while another involved kidnapping attempts. Iza allegedly paid these officers $280k a month for their “services,” like forcing rivals to hand over assets.
Iza’s scheme came to light after he stiffed a private investigator, triggering a cascade of lawsuits and criminal investigations. His girlfriend, also allegedly involved, is now dating the star of reality TV show Love Island. This tale has everything—crypto, hackers, corrupt cops, and reality show romance! With corrupt deputies, stolen millions, and custom legs, this saga truly stretches the limits of what we thought possible in cybercrime. (Krebs on Security)
Critical NVIDIA flaw affects AI applications
Researchers at Wiz have disclosed a critical vulnerability (CVE-2024-0132) affecting NVIDIA Container Toolkit and GPU Operator. The flaw affects any AI application that uses the toolkit to enable GPU support. NVIDIA issued a patch on September 26th.
Wiz stated, “The vulnerability enables attackers who control a container image executed by the vulnerable toolkit to escape from that container and gain full access to the underlying host system, posing a serious risk to sensitive data and infrastructure.” The researchers add, “The urgency with which you should fix the vulnerability depends on the architecture of your environment and the level of trust you place in running images. Any environment that allows the use of third party container images or AI models – either internally or as-a-service – is at higher risk given that this vulnerability can be exploited via a malicious image.” (Wiz, Nvidia)
North Korean hackers breach German missile manufacturer
North Korean hackers linked to the Kimsuky APT group successfully targeted Diehl Defence, a German missile manufacturer, by using spear-phishing emails with fake job offers. The attack involved booby-trapped PDF files and advanced social engineering tactics designed to steal login credentials. The breach marks major concerns due to the sensitive nature of the manufacturer’s work on air defense systems, including a recent contract with South Korea. (Security Week)
State CISO’s struggle with budget constraints
As per the story above, it seems a local community is being hit by a cyberattack every week, and new research shows why that might be. According to a new report from Deloitte and the National Association of Chief Information Officers (NASCIO), nearly 40% of U.S. state CISOs believe their cybersecurity budgets fall short of what they need to keep their citizens safe. In fact, more than a third stated they do not have a dedicated cybersecurity budget. The majority of CISOs surveyed said third-party breaches were the biggest threat they currently face, followed by AI-enabled attacks and foreign state-sponsored espionage. (InfoSecurity Magazine)
Have questions? Reach out to RedSeal today to chat with one of our cybersecurity experts or schedule a demo today.







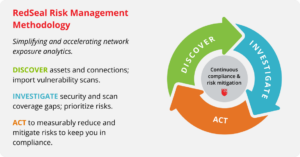 Today, let’s dive into one of our standout features—the Risk tab—and explore how we can use our Risk Management Methodology of Discover, Investigate, and Act to transform your risk management strategy.
Today, let’s dive into one of our standout features—the Risk tab—and explore how we can use our Risk Management Methodology of Discover, Investigate, and Act to transform your risk management strategy.