This week, CISA issues warnings about Cisco device vulnerabilities, while APT42 targets U.S. presidential campaigns. A Tennessee man is arrested for aiding North Korean IT schemes, and a severe CPU flaw from AMD raises alarms. Plus, GPS spoofing hacks are grounding commercial airliners, researchers uncover flaws in Georgia’s voter portal, and ransomware operators exploit ESXi hypervisors for mass encryption. We’ve rounded up the highlights from this week’s headlines on critical issues shaping the digital security landscape.
CISA warns of actively exploited Cisco devices
CISA has warned organizations about threat actors exploiting improperly configured Cisco devices, specifically targeting the legacy Cisco Smart Install (SMI) feature. Malicious hackers are acquiring system configuration files, which can lead to network compromises. CISA noted the continued use of weak password types on Cisco devices, making them vulnerable to password cracking attacks. Additionally, Cisco disclosed critical vulnerabilities in their end-of-life Small Business SPA IP phones, which can be remotely exploited but will not receive patches. (SecurityWeek)
Iran’s APT42 targets US presidential campaigns
Google’s Threat Analysis Group (TAG) has published a report on the Iran-aligned threat actor APT42’s targeting of US presidential campaigns. Google confirms that APT42 has targeted both the Trump and Biden-Harris campaigns with spearphishing attacks: “In May and June, APT42 targets included the personal email accounts of roughly a dozen individuals affiliated with President Biden and with former President Trump, including current and former officials in the U.S. government and individuals associated with the respective campaigns. We blocked numerous APT42 attempts to log in to the personal email accounts of targeted individuals.” TAG adds that the group “successfully gained access to the personal Gmail account of a high-profile political consultant.” The researchers note that APT42 has also ramped up its phishing attacks against users in Israel, targeting “people with connections to the Israeli military and defense sector, as well as diplomats, academics, and NGOs.” (Google)
Tennessee man arrested for alleged participation in North Korean employment scheme
The US Justice Department has arrested a man in Nashville, Tennessee, for allegedly helping North Korean IT workers get remote jobs at companies in the US and the UK. Matthew Isaac Knoot is accused of running a “laptop farm” to make the North Korean workers appear as if they were located in the US. The Justice Department stated, “The victim companies shipped laptops addressed to ‘Andrew M.’ to Knoot’s residences. Following receipt of the laptops, and without authorization, Knoot logged on to the laptops, downloaded and installed unauthorized remote desktop applications, and accessed the victim companies’ networks, causing damage tqqq o the computers. The remote desktop applications enabled the North Korean IT workers to work from locations in China, while appearing to the victim companies that ‘Andrew M.’ was working from Knoot’s residences in Nashville. For his participation in the scheme, Knoot was paid a monthly fee for his services by a foreign-based facilitator who went by the name Yang Di.”
The Justice Department says North Korea’s remote IT workers “have been known individually earn up to $300,000 annually, generating hundreds of millions of dollars collectively each year, on behalf of designated entities, such as the North Korean Ministry of Defense and others directly involved in the DPRK’s UN-prohibited WMD programs.” (DOJ)
Researchers find flaws in Georgia voter portal
Security researcher Jason Parker alerted ProPublica and Atlanta News First of a flaw in a portal run by the Georgia Secretary of State’s Office. This would allow someone to submit a voter cancellation request for anyone in the state. Parker said they attempted to contact the Secretary of State’s Office but did not receive a response. The portal launched on July 29th and already garnered attention for exposing driver’s license numbers. Parker found that by inspecting the portal’s source HTML, anyone could delete code requiring them to submit a driver’s license number and proceed to request a voter cancellation. The state eventually patched the issues, but security researcher Zach Edwards told ProPublica “It’s shocking to have one of these bugs occur on a serious website.” (ProPublica)
AMD SinkClose flaw helps install nearly undetectable malware
A warning from chip maker AMD about a high-severity CPU vulnerability which has been named SinkClose. The vulnerability affects multiple generations of its EPYC, Ryzen, and Threadripper processors, and allows attackers with Kernel-level (Ring 0) privileges to gain Ring -2 privileges and install malware that becomes nearly undetectable. For context, “Ring -2 is one of the highest privilege levels on a computer, running above Ring -1 (used for hypervisors and CPU virtualization) and Ring 0, which is the privilege level used by an operating system’s Kernel.” SinkClose has apparently passed undetected for almost 20 years.(BleepingComputer)
Ransomware operators exploit ESXi hypervisor vulnerability for mass encryption
Microsoft has also uncovered a vulnerability in ESXi hypervisors which it says is being exploited by “several ransomware operators to obtain full administrative permissions on domain-joined ESXi hypervisors.” The vulnerability “involves a domain group whose members are granted full administrative access to the ESXi hypervisor by default without proper validation.” Microsoft has disclosed the findings to VMware, and recommends that administrators apply the updates released by VMware. (Microsoft)
GPS spoofers hack clocks on commercial airliners
The relatively recent phenomenon of GPS spoofing involves hackers modifying GPS signals used by commercial airlines to navigate. The technique is also used to disorient drones and missiles in conflict zones. But now, according to Ken Munro, founder of British cybersecurity firm Pen Test Partners, and speaking recently at DEF CON, the technology is being used to change the times and dates on the clocks in aircraft cockpits, sometimes by years, Causing the plane to lose access to its digitally-encrypted communication systems, and requiring them to be grounded for weeks while engineers manually reset their onboard systems. (Reuters)
At Defcon, researchers reveal significant vulnerabilities in Google’s Quick Share
At Defcon 32, researchers Or Yair and Shmuel Cohen from SafeBreach revealed significant vulnerabilities in Google’s Quick Share, a peer-to-peer file transfer utility for Android, Windows, and Chrome OS. Quick Share uses various protocols like Bluetooth and Wi-Fi Direct, but these were not originally designed for file transfers. The researchers identified ten vulnerabilities, including a critical Remote Code Execution (RCE) flaw on Windows systems, dubbed QuickShell. This RCE exploit combines five of the vulnerabilities, allowing attackers to bypass security controls and take full control of target devices. The flaws also enable attackers to force file downloads and hijack Wi-Fi connections. Google has acknowledged the seriousness of these issues, assigning CVEs to two of the vulnerabilities. (Hack Read)
U.S. operation of “laptop farm” for North Korea shutdown
Tennessee resident Matthew Isaac Knoot has been arrested for allegedly running a ‘laptop farm’ to help North Korean IT workers secure remote jobs with American companies. Here’s how the scheme worked: Knoot would steal the identities of U.S. citizens and pose as U.S.-based IT professionals. Once hired, the company would send the work laptop to Knoot’s home, which he then gave the North Koreans access to, allowing them to log in remotely. If convicted, Knoot could face up to 20 years in prison, including a mandatory minimum of two years for aggravated identity theft. (Security Week)
Millions on the line as AI Teams advance in security challenge
Ninety teams competed at DEF CON over the weekend in the Artificial Intelligence Cyber Challenge hosted by the U.S. government’s Defense Advanced Research Projects Agency (DARPA) to develop autonomous tools that can find and fix vulnerabilities in open-source software. Twenty-two unique vulnerabilities were discovered in major open-source programs like the Linux kernel, with 15 automatically patched. The seven finalists are now tasked with building out their AI systems before the final competition at the 2025 DEF CON, with nearly $30 million up for grabs in prize money. (CyberScoop)
South Korean government says North Korean hackers stole tank and spy plane information
The South Korean government says North Korean hackers stole sensitive information on South Korea’s tanks and spy planes, BleepingComputer reports. The spy plane data was reportedly stolen from a South Korean defense contractor that produces operating manuals for military equipment. BleepingComputer cites local media reports as saying that “the leakage of the K2 tank data occurred when engineers working on one of the tank’s part makers moved to a competing company, taking along with them in external storage drives design blueprints, development reports, and details about the tank’s overpressure system.” (People Power Party, Bleepingcomputer)
NIST finalizes post-quantum encryption standards
On Tuesday, the National Institute of Standards and Technology (NIST) published three new encryption algorithms to bolster global cybersecurity efforts against future attacks using quantum technologies. The new standards are designed for general encryption and digital signatures. The algorithms, called FIPS 203, FIPS 204, and FIPS 205, are published to NIST’s post-quantum cryptography (PQC) project website. Head of the PQC project, Dustin Moody, urges security practitioners to immediately begin using the new algorithms to keep their data secure. (Dark Reading)
Orion loses $60 million in BEC scam
Luxembourg-based company, Orion, who is a leading supplier of carbon black, a material used to make tires, ink, batteries, and plastics was tricked into making several wire transfers through a Business Email Compromise (BEC) attack. According to documents filed with the Securities and Exchange Commission (SEC), a non-executive employee “was the target of a criminal scheme that resulted in multiple fraudulently induced outbound wire transfers to accounts controlled by unknown third parties.” Orion expects to record “a one-time pre-tax charge of approximately $60 million.” if the funds are not recovered. (The Record)
Azure AI health bot infected with critical vulnerabilities
Multiple privilege escalation issues in Microsoft Azure’s cloud-based Health Bot service exposed the platform to server-side request forgery (SSRF) and access to cross-tenant resources. The Azure AI Health Bot Service enables healthcare organizations to build their own virtual health assistants to interact with patients and manage administrative workloads. Depending on the nature of the integration, the chatbots could potentially have privileged access to extremely sensitive health information. Researchers at Tenable, who identified the issues said, though Microsoft quickly patched the vulns, they showcase inherent concerns about chatbot risks. (Dark Reading)
Palo Alto Networks patches several vulnerabilities
Palo Alto Networks has issued patches for several vulnerabilities, including the high-severity CVE-2024-5914, which affects the Cortex XSOAR product. This flaw allows unauthenticated attackers to execute commands within certain configurations. Patches are available starting with version 1.12.33. Additionally, updates were released for Prisma Access Browser, addressing over 30 vulnerabilities in the Chromium-based browser. Two medium-severity flaws were also patched, impacting PAN-OS and the GlobalProtect app. Palo Alto Networks is not aware of any active exploitation of these vulnerabilities. (SecurityWeek)
Microsoft patches zero-click RCE vulnerability
Microsoft has issued a patch for a zero-click remote code execution vulnerability (CVE-2024-38063) that affects all Windows machines using IPv6, which is enabled by default, BleepingComputer reports. Microsoft says “[a]n unauthenticated attacker could repeatedly send IPv6 packets, that include specially crafted packets, to a Windows machine which could enable remote code execution.” The vulnerability was discovered by a researcher at Kunlun Lab, who noted that the bug is triggered before the packet reaches the Windows firewall. There’s no evidence of exploitation so far, but Microsoft has given the flaw its “Exploitation more likely” label. Users are urged to update Windows as soon as possible or disable IPv6 until patches can be applied. (Bleepingcomputer)
Massive cyberattack hits Central Bank of Iran and other Iranian banks
News agency Iran International has reported a massive cyberattack that has disrupted the operations of the Central Bank of Iran (CBI) along with several other banks in the country, disabling the computer systems of many banks in the country. As reported in Security Affairs, “this incident coincides with intensified international scrutiny of Iran’s operations in the Middle East,” amid announcement from Tehran regarding attacks on Israel as well as its widely reported attempts to influence the upcoming U.S. Presidential election. According to the news agency, this is one of the largest cyberattacks on Iran’s state infrastructure to date. (Security Affairs)
Kim Dotcom to be extradited from New Zealand
After a 12-year fight, the infamous Kit Dotcom is being extradited to the U.S. to face criminal charges relating to the operations of his now closed file-sharing website Megaupload. Dotcom, whose real name is Kim Schmitz, holds Finnish and German nationalities and has been living in New Zealand, and has faced numerous charges since the mid-1990s for computer fraud, data espionage, and many other nefarious activities. U.S. authorities say, “Dotcom and three other Megaupload executives cost film studios and record companies more than $500 million by encouraging paying users to store and share copyrighted material, which generated more than $175 million in revenue for the website.” (Reuters)
Have questions? Reach out to RedSeal today to chat with one of our cybersecurity experts.




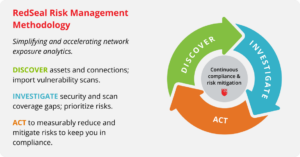 Today, let’s dive into one of our standout features—the Risk tab—and explore how we can use our Risk Management Methodology of Discover, Investigate, and Act to transform your risk management strategy.
Today, let’s dive into one of our standout features—the Risk tab—and explore how we can use our Risk Management Methodology of Discover, Investigate, and Act to transform your risk management strategy.


